Cryptography is the basis that characterizes the procedures that are carried out through the use of BitIQ, where messages are sent between two or more parties through data encryption.
Mainly, the transmission of messages is done secretly; nobody knows the sender or the receiver; consequently, they use pseudonyms.
Cryptographic operations guarantee security and trust levels depending on the encryption level that the messages possess to avoid the use of third parties for the confirmation of operations.
With the encryption of information, most companies keep their data safe from what we now know as hacking.
This type of technology guarantees that the transactions carried out does not require the data of the people who carry out the operations, much less financial data of a banking nature such as TDC or debit cards.
Even if the device or the servers where the information is stored is lost, the data will be inviolable if the encryption is correct.
The encryption of the information is of the utmost importance for cryptocurrencies, and the parties involved are responsible for developing the data transmission processes.
The mathematical algorithms make up the files that are transmitted from one point to another simultaneously and where the participants are the ones that validate whether the transaction is correct or not.
Encryption does not only happen in the field of cryptocurrencies; from the searches we do on the internet, an email to a text message from our phones is encrypted.
Importance of encryption

When the creator of Bitcoin, the pseudonym of Satoshi Nakamoto, proposed the idea of this digital currency that came to revolutionize the financial market, he defined cryptography as the basis of the processes with any of the digital currencies.
Nakamoto cryptographically solves the inconvenience that arise called double-spending. Through public and private keys, it is possible to carry out reliable and secure operations between people who do not know each other.
All this without using a third party to validate the transactions; these intermediaries are represented by financial entities such as banks.
Definition of public key and private key
When talking about public and private keys, direct reference is made to the methods used in the blockchain platform to decrypt and therefore decrypt the data contained in a cryptographic message or operation.
These keys are based on mathematical algorithms, where any participant can know the public keys. In contrast, the private keys must be stored with suspicion in safe places to protect users’ information or digital assets.
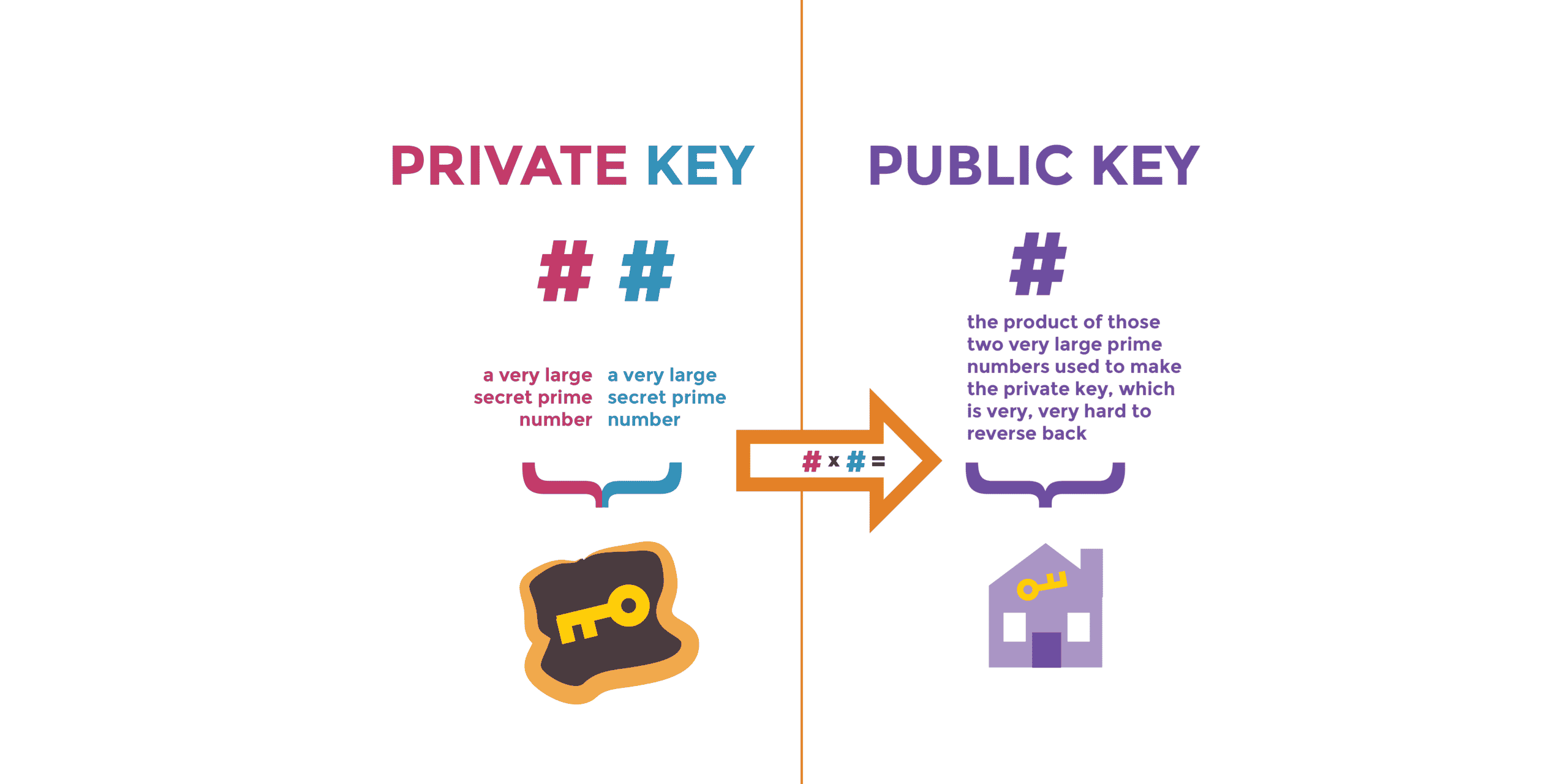
Depending on the type of cryptocurrency used, the private keys will be different from one currency to another; this type of encryption is transmitted in the form of bits.
The most common example when we refer to public and private keys is reflected in digital wallets.
In the specific case of wallets, when talking about the public key, it refers directly to the address of a user X; this serves as a means of approving access to other users to carry out transactions towards that wallet, and the private key will be essential to confirm the operation being performed.
Types of encryption according to the kind of key
As any computer procedure requires a classification that is why both public and private keys can be encrypted in different ways, among which we find:
-
Asymmetric encryption
This type of encryption is based on using a public key to create a summary of the content of the message and a private key to decrypt it. The best-known methods for this type of encryption are ElGamal and RSA.

This type of encryption aims to keep the operation as authentic as possible, avoiding the loss of information during the transmission process.
-
Symmetric encryption
Unlike asymmetric encryption, the same key is used to create the content and decrypt its data. The most used methods in this type of encryption are AES, DES, and triple DES.
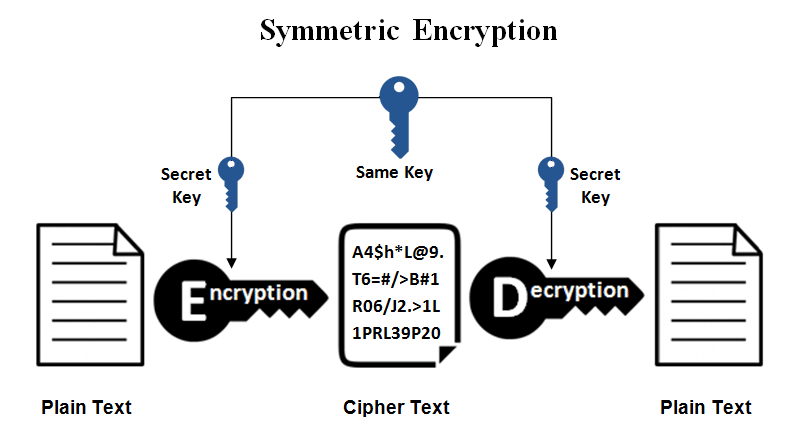
This unique key is characterized by the fact that it can be the same or different between the parties. The important thing is to receive and validate the information to be decrypted.
Conclusion
Every time more information is acquired regarding the processes and concepts used during cryptocurrency transactions, they are safe and reliable operations become clearer.
Also Checkout: DAY TRADING OR SWING TRADING WHICH ONE IS THE BEST OPTION?















