The Wire investigates charges that cyber operatives used ‘Tek Fog,’ a highly sophisticated app, to hijack key social media and encrypted messaging platforms and broadcast right-wing propaganda to a domestic audience.
An anonymous Twitter account claiming to be a dissatisfied employee of the Bharatiya Janata Party’s (BJP) Information Technology Cell (IT Cell) claimed the existence of a highly sophisticated and secret app dubbed ‘Tek Fog’ in a series of tweets in April 2020.

They stated that political operatives linked to the ruling party use the app to falsely inflate the party’s popularity, harass critics, and alter public perceptions on a large scale across key social media platforms.
As per the Report of The Wire, their authors were intrigued by the Twitter handle’s mention of Tek Fog, a ‘secret app’ that could ‘bypass reCAPTCHA protocols’ and allow co-workers to ‘auto-upload texts and hashtag Trends,’ so they reached out to the person behind the account to learn more about it.
During further chats, the insider said that their daily jobs included using the Tek Fog app to hijack Twitter’s ‘trending’ area with selected hashtags, creating and managing various WhatsApp groups linked with the BJP, and direct online harassment of journalists critical of the BJP.
They decided to come forward after their alleged handler – Devang Dave, the former national social media and IT head of the Bharatiya Janata Yuva Morcha (the BJP’s youth wing) and current Maharashtra election manager – failed to deliver on a lucrative job offer promised in 2018 if the BJP could retain power in the 2019 Lok Sabha elections.

Each of the informant’s charges was subjected to an independent verification procedure in which the team sought to learn more about the app’s many features, the identities of the app’s authors, its users, and the organizations that allowed it to be used.
The person behind the Twitter account supplied multiple screencasts and screenshots showing the app’s features via encrypted emails and online chat rooms. The source also gave their pay stubs and bank records in order to prove their identity (under the condition that it not be made public) and that of their employers.
The Tek Fog app was not directly accessible from the source. They claimed that this was due to the existence of several security constraints, such as the need for three one-time passwords (OTPs) to enter into the app dashboard and the usage of a local firewall to prohibit access from outside the facility.

They were able to link us to a BJYM official via email, who offered code scripts that assisted the team in identifying the different external tools and services connected to the secure server that hosted the Tek Fog app.
Furthermore, they used a variety of open-source investigative techniques in addition to the primary evidence provided by the source to undertake a thorough forensic investigation of the numerous social media assets provided by the source and to corroborate the network infrastructure backing the use of the app. In order to gain a better understanding of the network, the team also spoke with other independent specialists and current workers at the companies involved.
They were able to build on these initial shards of evidence to uncover a massive operation pointing to the existence of a group of public and private actors working together to subvert public discourse in the world’s largest democracy by driving inauthentic trends and hijacking conversations across nearly all major social media platforms.
4 Troubling Features of Tek Fog
The source’s screencasts and screenshots of Tek Fog highlighted the app’s various features, allowing the team to learn more about the network of cyber troops who use it on a daily basis to manipulate public discourse, harass and intimidate independent voices, and maintain a partisan information environment in India.
- The Construction of a public narrative
One of the app’s main objectives is to take over Twitter’s ‘trending’ area and make it ‘trend’ on Facebook. This method employs the app’s built-in automation tools to ‘auto-retweet’ or ‘auto-share’ individual or group tweets and posts, as well as spam existing hashtags with accounts controlled by app operatives.
This tool is also used to boost right-wing misinformation on the platform, exposing it to a wider audience and making extreme narratives and political campaigns appear more popular than they are.
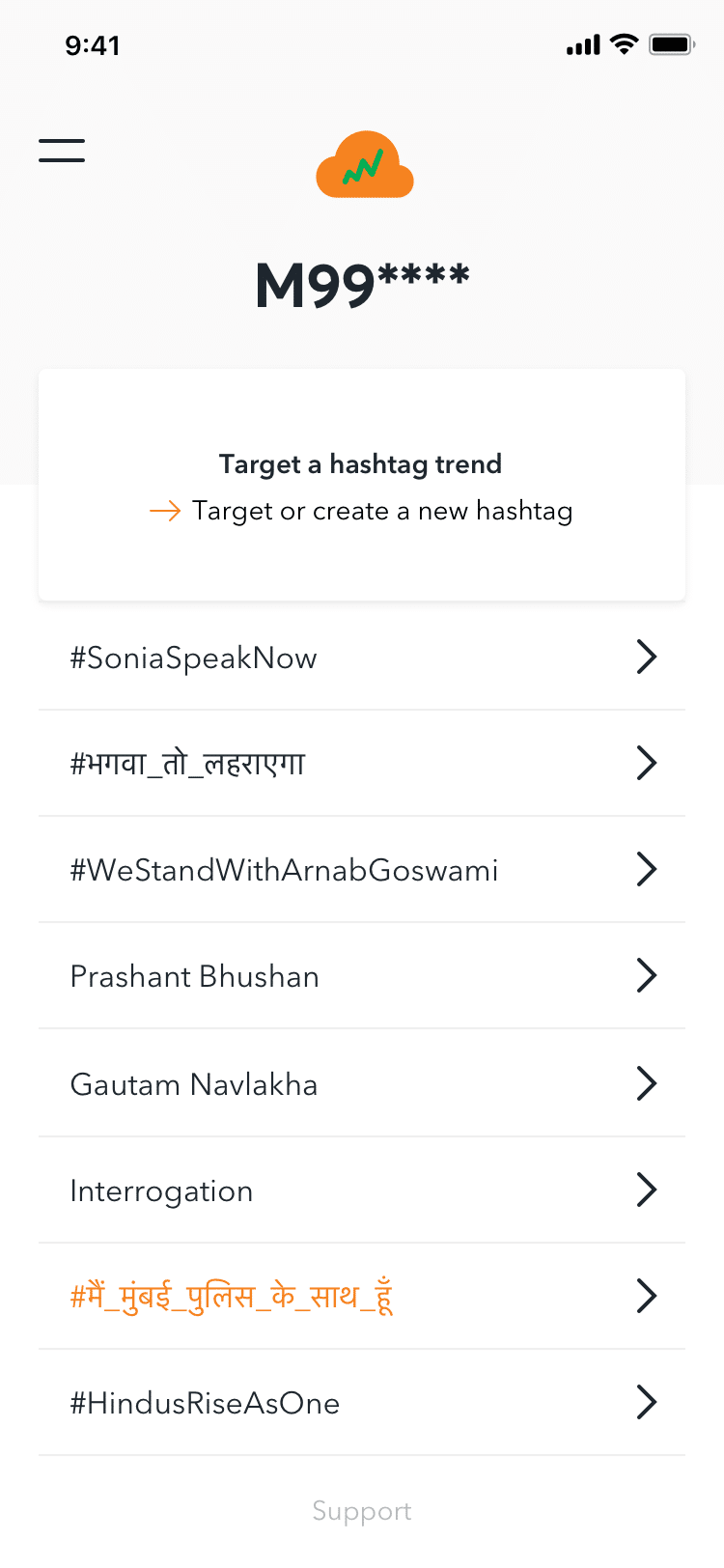
The source revealed one of the hashtags – #CongressAgainstLabourers – as part of a screenshot exposing their ‘daily job’ list for that day at 8:25 p.m. IST on May 4, 2020. The source was charged, according to the same screen, with getting the hashtag to appear in at least 55,000 tweets and enter the platform’s ‘trending’ section.
These identities are also generated utilizing in-app tools that allow individual operatives to generate ‘temporary’ email addresses, activate phone numbers, and bypass programming limits, as well as WhatsApp, Facebook, Instagram, Twitter, and Telegram’s email and OTP verification.
Their team couldn’t tell if these were ‘temporary’ accounts generated by the app or real BJP activists and app operatives who were connected to the app to enable planned publishing.
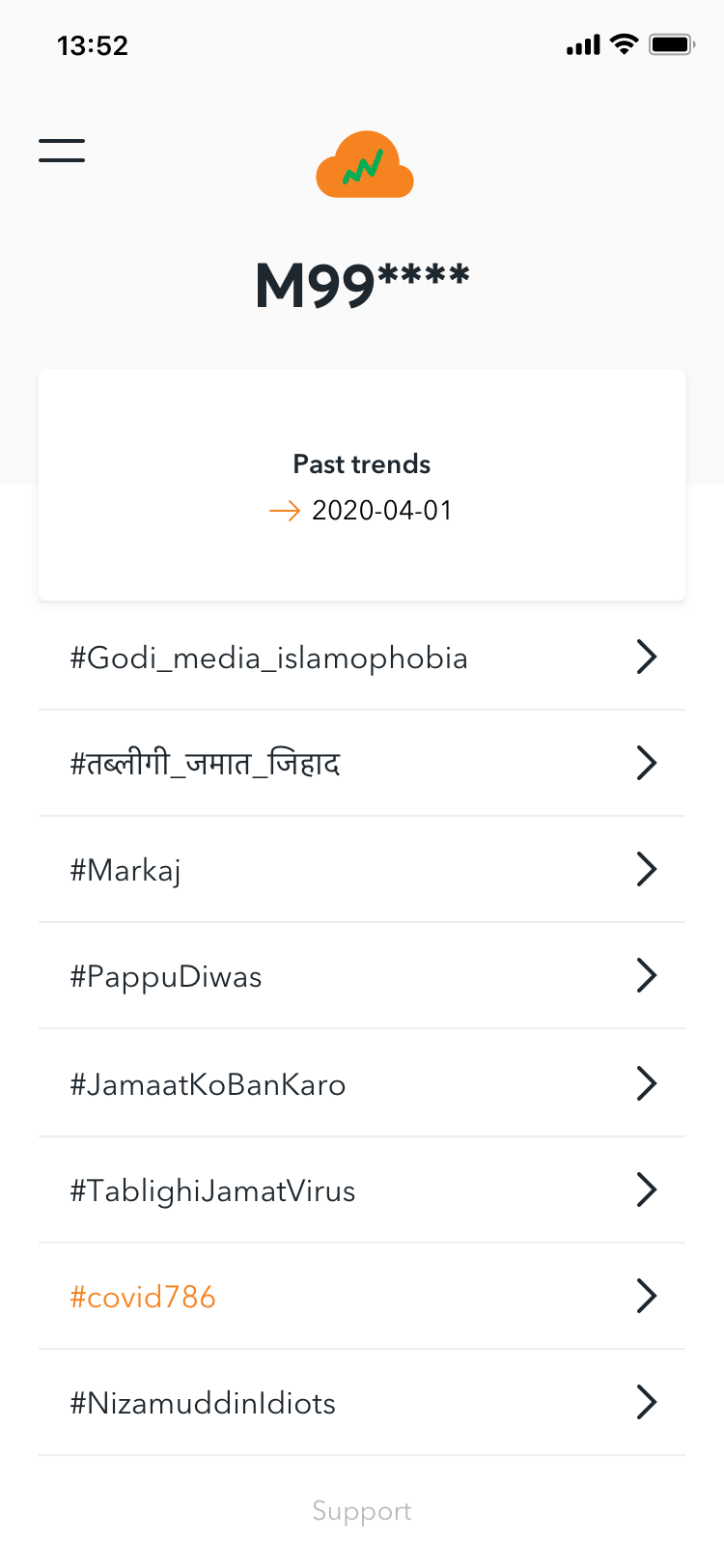
- Using ‘inactive’ WhatsApp accounts for phishing
Another concerning feature of the software is its capacity to allow individual agents to hijack ‘inactive’ WhatsApp accounts of ordinary people and use their phone numbers to message their ‘often contacted’ or ‘all contacts,’ similar to ‘token theft.’ This capability is also used by app operators to phish personal information from targeted users in order to upload it to a cloud-based political database. When private people are added to this database, they become potential targets for future harassment and trolling efforts.
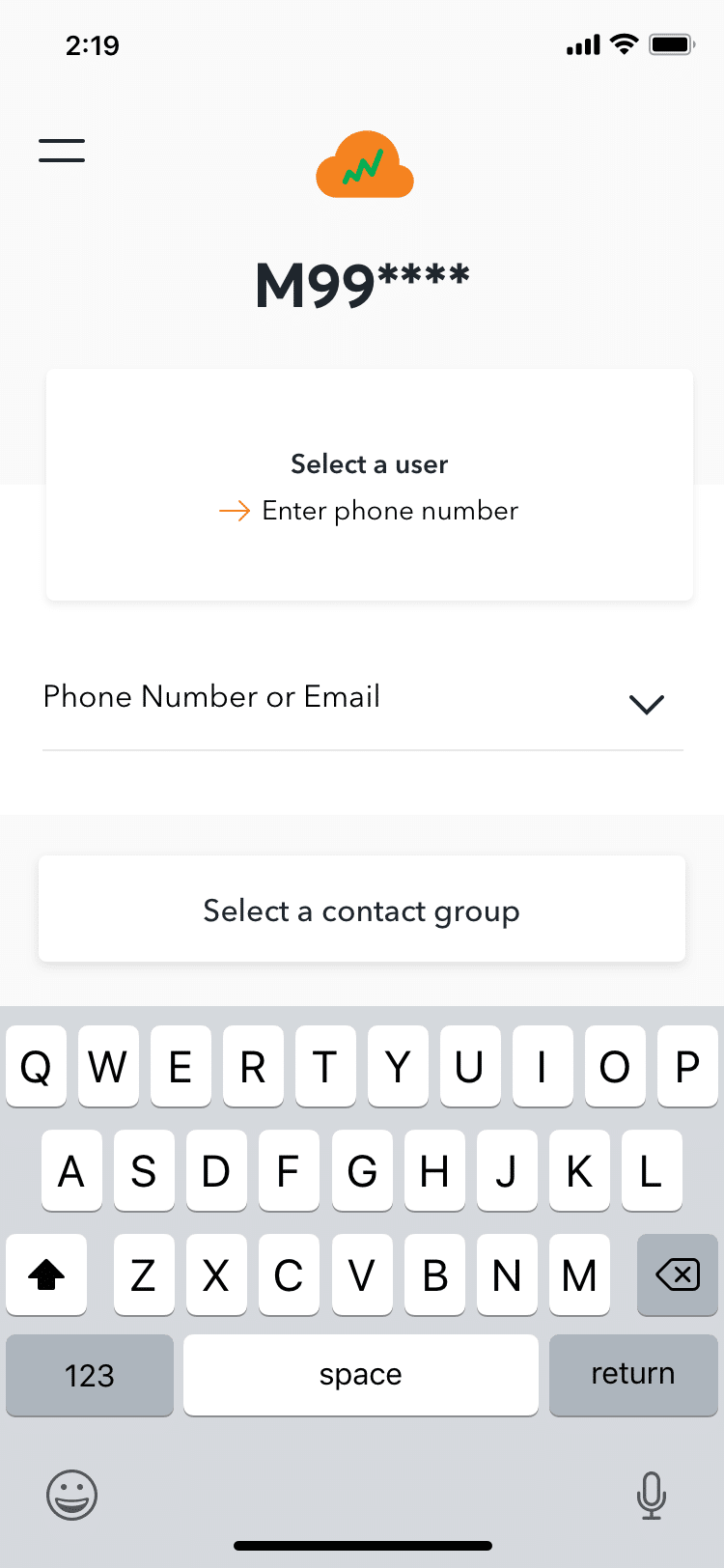
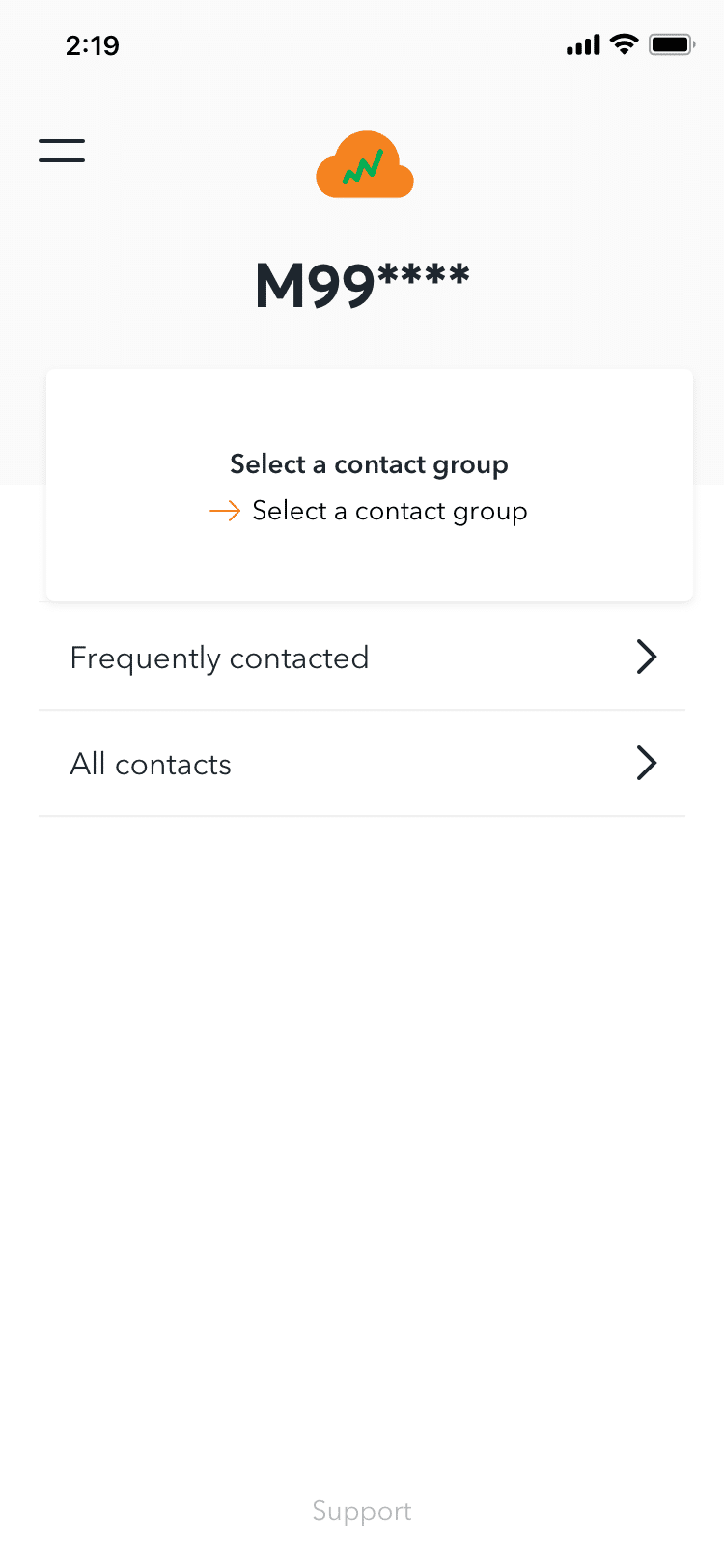
All of the top five users (including one of the other authors) received a custom text message indicating that this feature of the app was operational at the time of analysis.
- Harassment of private people based on a database
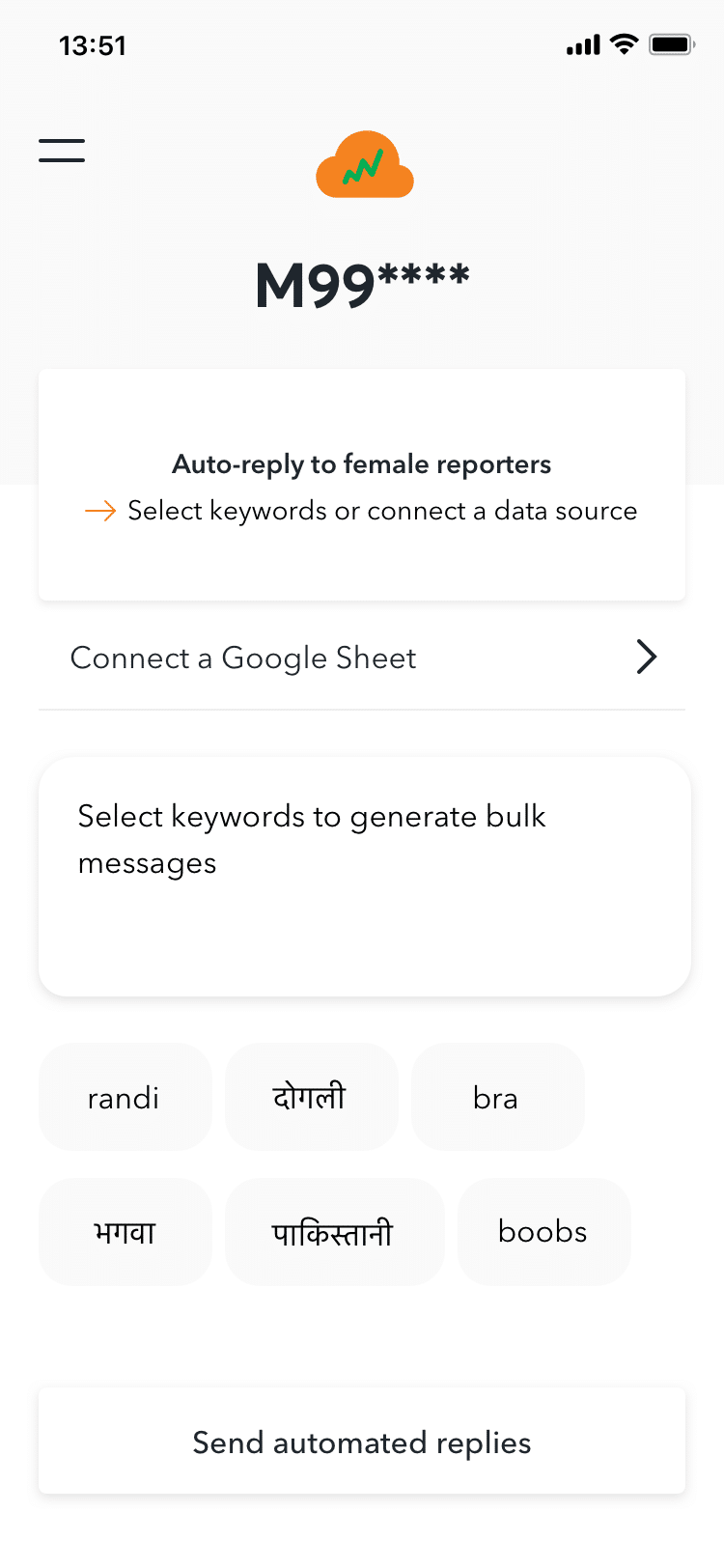
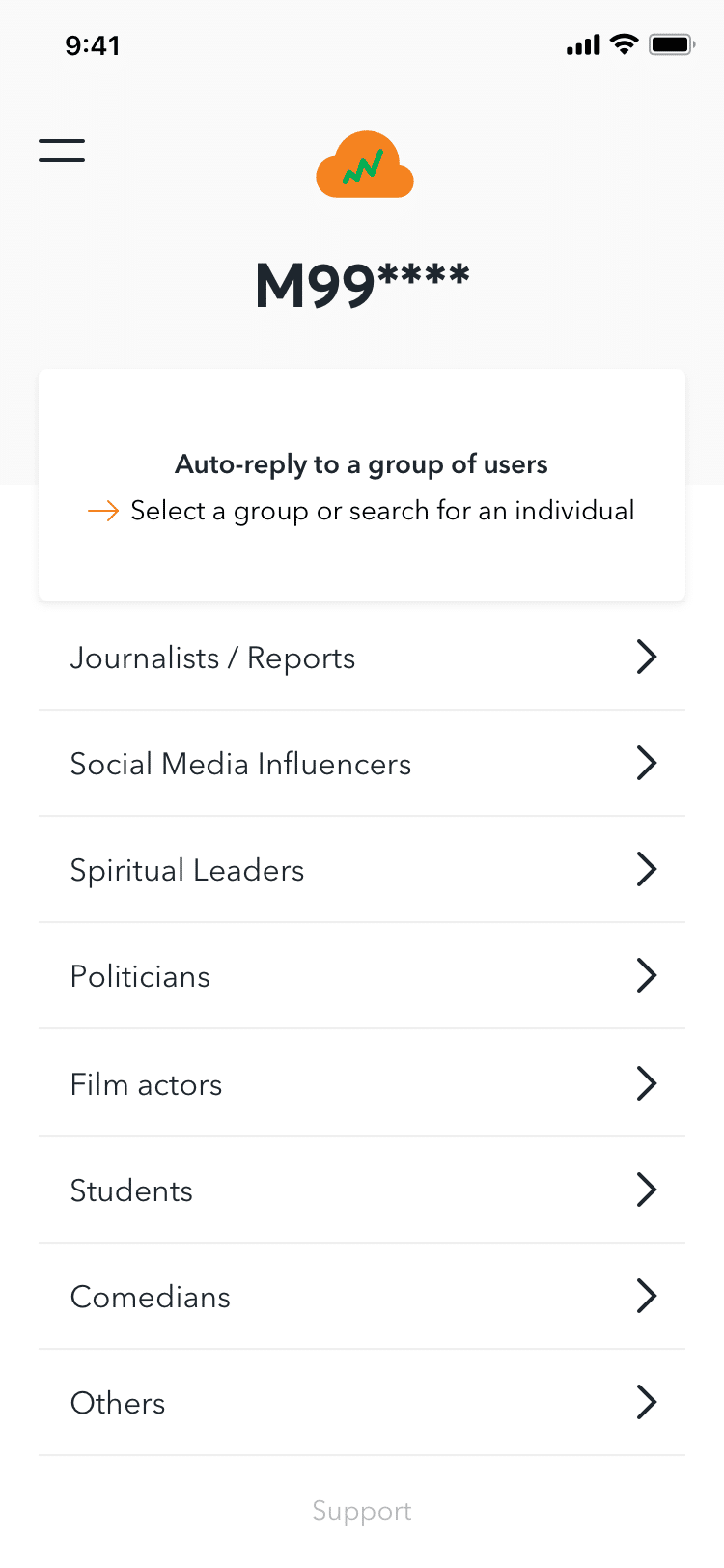
The app’s pictures and screencasts reveal a large and dynamic cloud database of private people organized by occupation, religion, language, age, gender, political leanings, and even physical characteristics. The pictures also show that by linking a Google Sheet or auto-generating keywords and phrases, app operatives can ‘auto-reply’ to individuals or groups, the great majority of which are hostile or insulting.
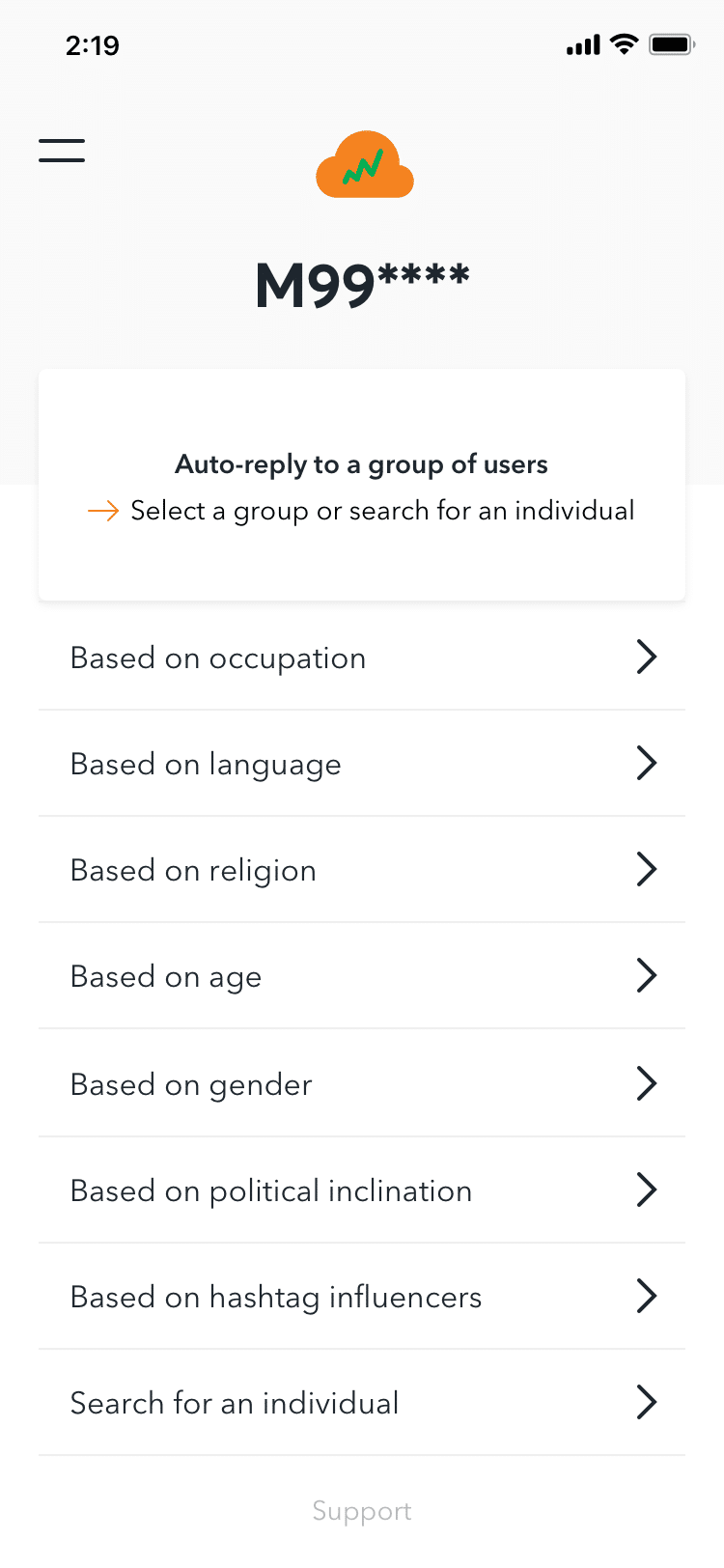
They couldn’t access any of the linked Google Sheets since the app’s operators don’t have a direct link to modify or see the documents; instead, they can only select available ‘inputs’ from an app’s auto-suggested menu. The BJP, on the other hand, has already used Google Sheets to distribute narratives, as reported by AltNews.
- There is no trace of what happened
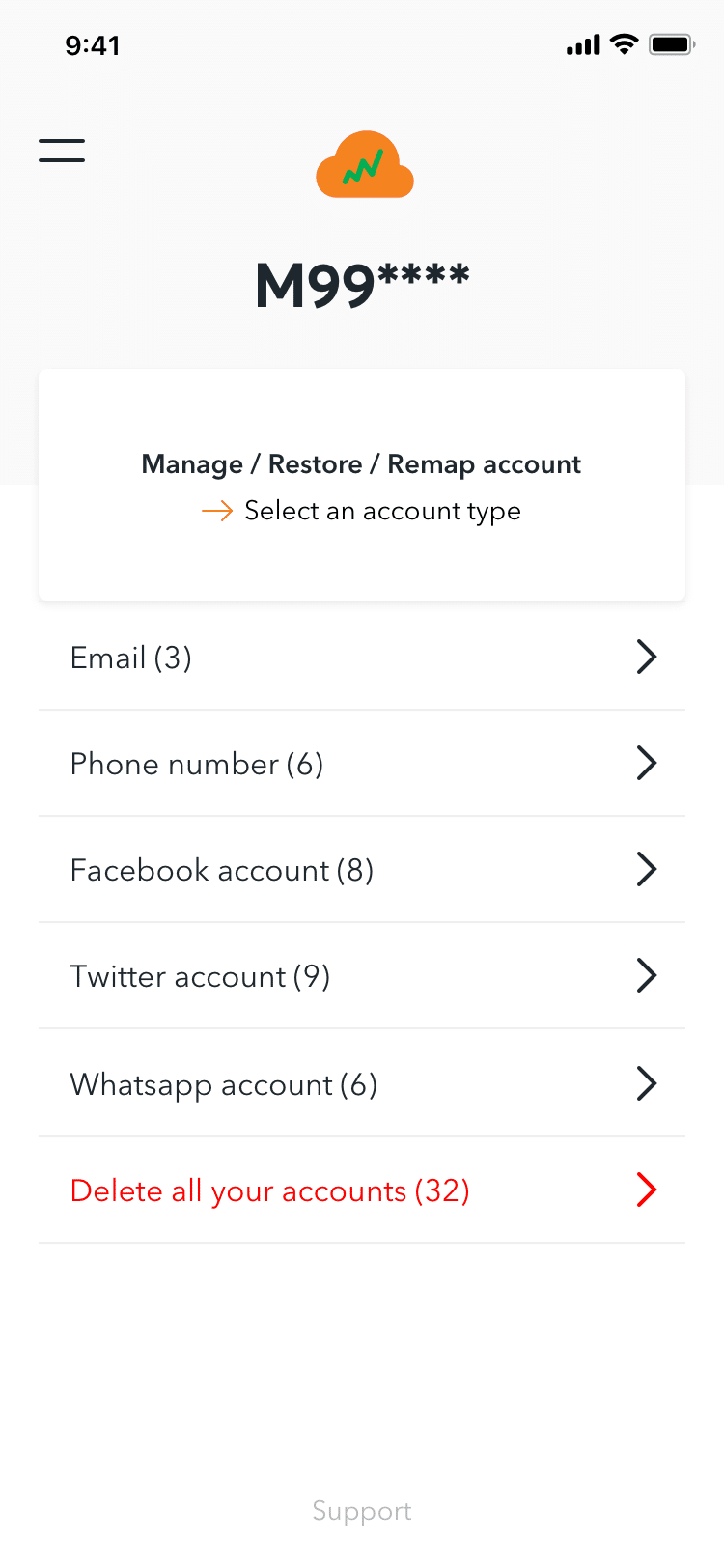
Another useful feature included in the app screens was the option for app administrators to delete or remap all existing accounts at any time. This capability permits them to hypothetically destroy all incriminating proof of their previous activities.

The Wire was unable to independently verify if the feature was active at the time of publication due to the nature of the feature.
Persistent Systems is linked with Tek Fog
Since 2015, Persistent Systems, a technology services company, has focused extensively on obtaining government contracts. Mritunjay Singh, the business’s then-executive director and president-services, stated in an interview with The Hindu Businessline in January 2018 that the company was “bullish on government expenditure on Information Technology to grow its profits.”

Persistent Systems was chosen by India’s Ministry of Health and Family Welfare to develop a digital data hub that would record, store, and process health information across ten Indian states a few months later, in July of the same year.

Twitter and WhatsApp integration, data input tools via Google forms, payment infrastructure via Paytm, and automation tools via Tasker – an Android app that triggers specific actions like sending a message based on inputted ‘contexts’ like user location, time, date, event, and gesture – are all suggested in technical documents.
Sharechat is being used to spread hate speech
The app’s agents allegedly utilized Sharechat, Mohalla Tech Pvt. Ltd.’s flagship tool, to test and curate fake news, political propaganda, and hate speech before spreading it to other prominent social media sites, including Twitter, Facebook, and WhatsApp, according to the source.
Sharechat, which bills itself as India’s #1 social networking app, includes dozens of regional communities that allow millions of users to share messages, news, images, memes, and videos in their native tongue. The software functions as a social network, allowing users to follow accounts and communicate with other users, as well as an open broadcasting platform, allowing users to share information with strangers.
Sharechat offers 14 distinct local languages and focuses on hyperlocal content for India’s growing non-English-speaking social media users, who are mostly from Tier 2 and Tier 3 cities. With a user base of 160 million in India, the firm raised $502 million from Tiger Global, Snap, and other previous investors such as Twitter in April 2021 and $145 million in a new investment round last July, valuing the company at roughly $3 billion.

During the 2017 Uttar Pradesh elections, Ankur Shrivastava, Sharechat’s product lead, wrote a Medium post about the company’s efforts to get political parties to use the social media platform. In the UP elections, this included building separate communities and tags for regional parties, as well as calculating a popularity index for each.
A year later, MoneyControl released an article describing how a number of regional and national parties had launched profiles on the vernacular platform in order to take advantage of the network’s most localized readership.
The source gave a list of 14 accounts managed by them via the Tek Fog app, each of which had a linked account on Sharechat, to validate their claim and provide more insight into the platform’s relationship to the bigger operation.
Also Checkout: Analysis Of Swachh Bharat Abhiyan 2.0















